2.1. Operational challenges
Institution-initiated reporting of cyber incidents by FIs is typically triggered by exceeding implicit or explicit criteria and is normally associated with specific reporting obligations, such as a requirement to submit letters of notification, complete incident templates or report via other online tools/platforms. Meaningful differences in how different authorities determine their reporting criteria for cyber incidents, use incident information and set their timeframes for reporting an incident pose operational challenges for FIs; particularly for FIs that operate across many jurisdictions and sectors and are subject to multiple reporting requirements for one incident, with each report tending to trigger follow-up enquiries from each financial authority. In addition, many FIs are required to report to law enforcement, cyber insurance, industry threat sharing groups, customers and stakeholders within set timeframes, as well as internally to business continuity teams, corporate executives and corporate communication teams. At the same time, incident response teams are working to address the incident, minimise the harm and recover operations as quickly as possible.
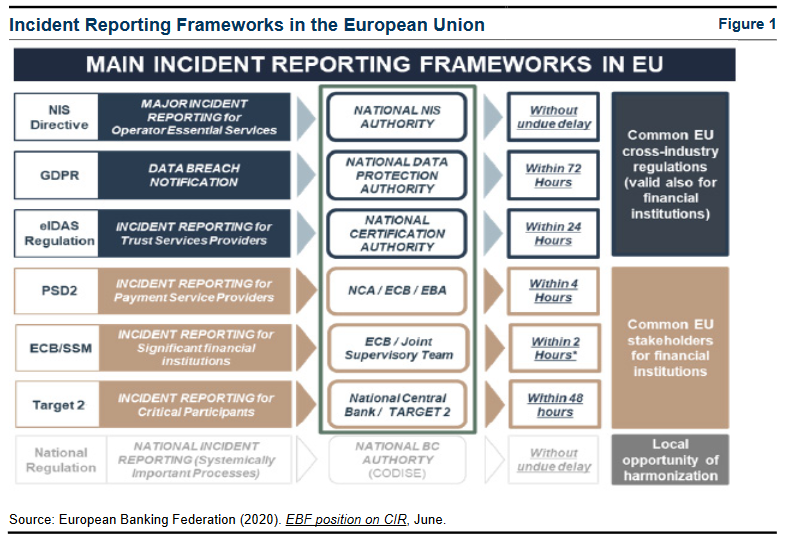
Figure 1 illustrates how FIs operating in the European Union (EU) have to report incidents to multiple authorities under different EU regulations/directives and under different timeframes, ranging from 'without undue delay' to 'within 72 hours'. The reporting process involves authorities at both the national and European level, often applying different procedures, criteria/thresholds, templates and taxonomy. The newly developed Digital Operational Resilience Act (DORA) is a step towards harmonisation of incident reporting requirements across the EU, paving the way towards a centralised EU incident hub.